Background¶
The global deployment of a Resource Public Key Infrastructure (RPKI [1]) is one step towards securing the Internet routing through cryptography. The RPKI allows the holder of a distinct IP prefix to authorize certain autonomous systems (AS) to originate corresponding routes, which is cryptographically verifiable through Route Origination Authorizations (ROAs) that are stored in the RPKI.
RPKI enabled routers do not store such ROAs themselves, but only the validated content of those. To achieve high scalability as well as limit resource utilization on BGP routers, the validation of ROAs is performed by trusted RPKI cache servers, which are deployed at the network operator site. The RPKI-RTR protocol defines a standard mechanism to maintain exchange of the prefix origin AS relations between the cache server and routers. In combination with a BGP prefix origin validation scheme a router is able to verify received BGP updates without suffering from cryptographic complexity.
The RTRlib is a lightweight C library that implements the RPKI-RTR protocol for the client end (i.e., routers) and the proposed prefix origin validation scheme. The RTRlib provides functions to establish a connection to a single or multiple trusted caches using TCP and SSH transport connections, and further allows to determine the validation state of prefix to origin AS relations.
Fig. 1 shows a typical RPKI deployment, where trusted cache servers collect ROAs from global RPKI repositories of the RIRs, such as RIPE and APNIC. Each local RPKI cache periodically updates and verifies the stored ROAs, and pushes the preprocessed data to connected RPKI enabled BGP routers using the RTR protocol.
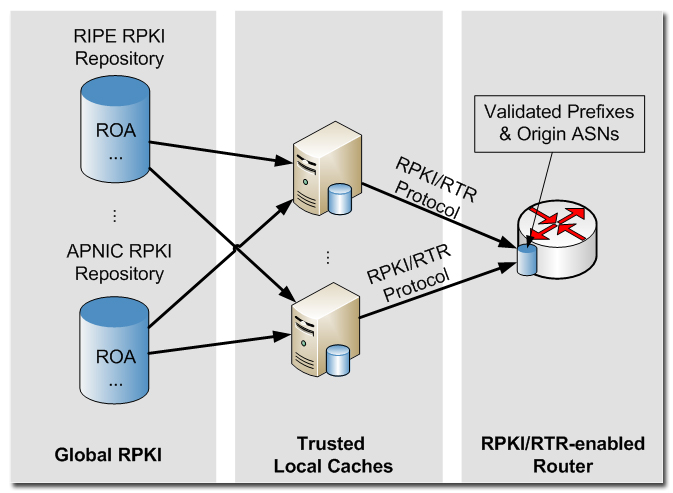
Fig. 1 Overview on a typical RPKI deployment, showing global RPKI repositories, trusted cache servers, and RPKI enabled BGP routers.
Further Reading¶
Detailed insights on the implementation of the RTRlib and its performance can be found in [2]. Further information is available in the standard specifications and protocols in RFCs 6810 [3] and 6811 [4], to which the RTRlib complies. Even more background material on BGP security extensions can be found in [5], [6], and [7]
References
| [1] | M. Lepinski and S. Kent. An Infrastructure to Support Secure Internet Routing. RFC 6480, IETF, February 2012. |
| [2] | Matthias Wählisch, Fabian Holler, Thomas C. Schmidt, and Jochen H. Schiller. RTRlib: An Open-Source Library in C for RPKI-based Prefix Origin Validation. In Proc. of USENIX Security Workshop CSET‘13. Berkeley, CA, USA, 2013. USENIX Assoc. URL: https://www.usenix.org/conference/cset13/rtrlib-open-source-library-c-rpki-based-prefix-origin-validation. |
| [3] | R. Bush and R. Austein. The Resource Public Key Infrastructure (RPKI) to Router Protocol. RFC 6810, IETF, January 2013. |
| [4] | P. Mohapatra, J. Scudder, D. Ward, R. Bush, and R. Austein. BGP Prefix Origin Validation. RFC 6811, IETF, January 2013. |
| [5] | S. Bellovin, R. Bush, and D. Ward. Security Requirements for BGP Path Validation. RFC 7353, IETF, August 2014. |
| [6] | Matthew Lepinski and Sean Turner. An Overview of BGPsec. Internet-Draft – work in progress 08, IETF, June 2016. |
| [7] | Matthew Lepinski and Kotikalapudi Sriram. BGPsec Protocol Specification. Internet-Draft – work in progress 19, IETF, November 2016. |